DIGITAL ELECTRONIC
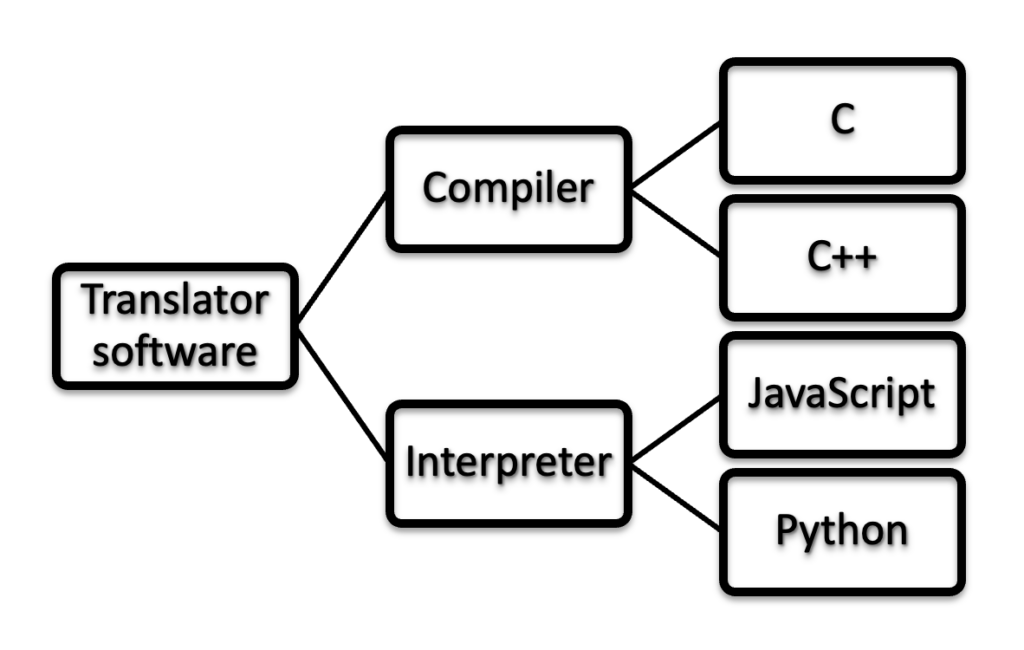
PHP is known as Hypertext Preprocessor. It is an open-source, server-side scripting language embedded in HTML used to manage databases, development of web applications, session tracking, build e-commerce sites, etc. It is kind of a programming language that is used for writing automated tasks. Many databases such as PostgresSQL, Oracle, Informix, MySQL can be integrated with PHP.
It supports a large number of protocols such as POP3, IMAP, and LDAP. PHP scripts are interpreted only on a server that has PHP installed in it. Since PHP is a server-side scripting language, it gets executed first on the server and then it gets to the web browser to the user.
Why is PHP so Common?
- Versatile:- PHP is platform-independent and can be run on multiple platforms such as Mac OS, Windows, Linux, and multiple browsers are also supported.
- Speed and Security:- PHP uses its memory for its overall functioning and hence has a good operational speed. Moreover, it has many new tools and frameworks are there in the market to protect against cyberattacks.
- Compatibility:- It is compatible with all the servers such as Apache, etc.
- Legacy Code:– Many websites are written with PHP, which gives an edge to make updates in the existing code rather than rewriting the new code.
- Open-Source:- PHP can be installed for free and quickly. This feature helps companies in controlling the cost of web development.
Uses of PHP
Encryption
PHP can be used to encrypt data. It assists with several extensions, like OpenSSL and Sodium, which eventually cover a wide variety of encryption algorithms. Before inserting the data into the database scripts encrypt it and decrypt it before retrieving it.
File Manipulation
It helps in creating, writing, deleting, opening, closing, and reading files on the server. Various commands are used for file manipulation which is listed below:
- PHP Read File:- The command is fread(). This function is used to read the content of the file.
- PHP Write File:- The command is fwrite(). This function is used to write the content of the string into a file.
- PHP Open File:- The command is fopen(). This function is used to open a file.
- PHP Close File:- The command is fclose(). All the open files are closed with the help of this function.
- PHP Delete File:- The command is unlink(). This function is used to delete files.
Handling Databases
Data can be added, deleted, modified within the databases using PHP. It gives the freedom to the developers to connect it securely with any kind of database. This gives them the freedom to choose which database is best suited for the application to be developed.
Dynamic Content
PHP helps in creating dynamic page content. Majorly, there are three types of dynamic information on the web which are stated below:
- Dynamic Web Pages:- A full web page is generated.
- Dynamic content:- Only a certain portion of web pages are generated.
- Dynamic Data:- Variables on a web page are generated.
Dynamic handling of web pages is a bit complicated if the scope of the information to be generated is vast. But, with the help of two PHP functions, include() and require() it has become easier.
Controlling Access
It helps in restricting and allowing access to the users for accessing the pages on the website. Various roles will be assigned to multiple users in an application. Accordingly, an access control system is designed. It can control user permissions based on the PHP pages or database records.
Cookies
PHP can set cookies and receive cookies. setcookie() function is used for creating cookies. isset() function is used to check if the cookie is set. There are other manipulations that can be done with PHP cookies such as Modify Cookie, Delete Cookie and check if Cookies are enabled.
Form Handling
It can handle form manipulation, i.e., collect data from files, send the data through email, return data to the user. Also, it can save data to the file.
Conclusion
Programming for the web is altogether a different experience than traditional programming. Web development is meant to ensemble multiple resources together, which in turn requires more tools. Multiple languages mean higher maintenance. To avoid such a situation PHP is the correct tool for in fact a complete package for web development.
The post PHP Uses – Applications of PHP appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/30WgW3O