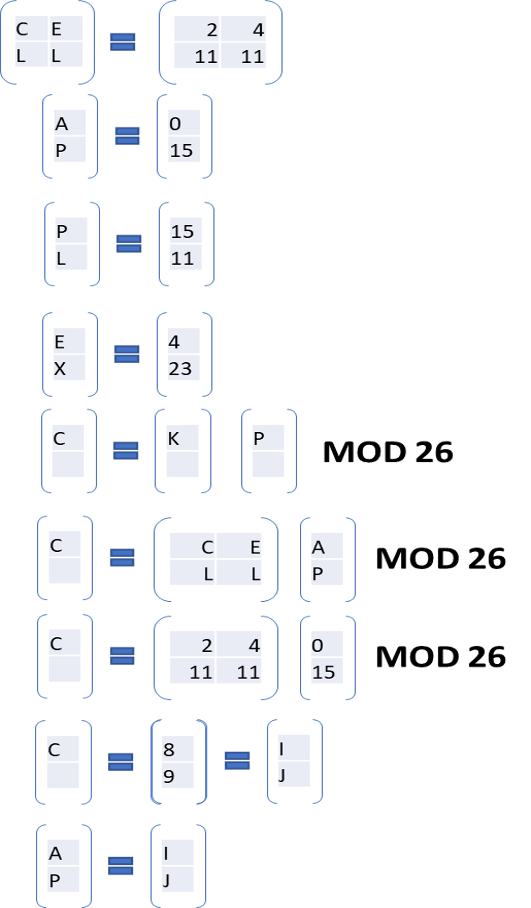
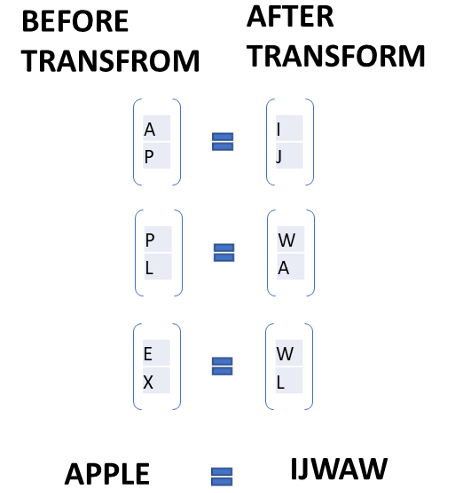
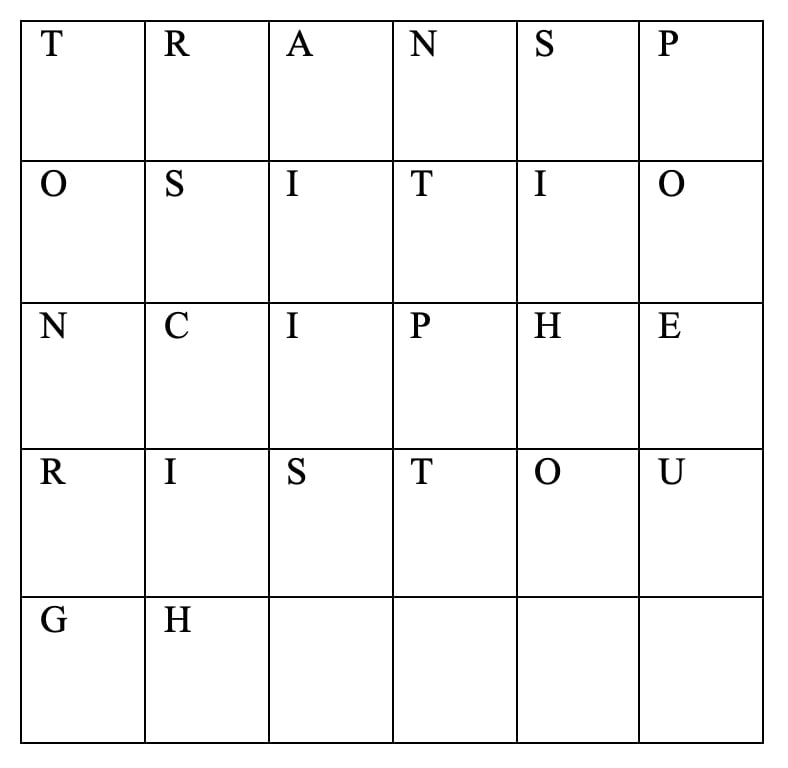
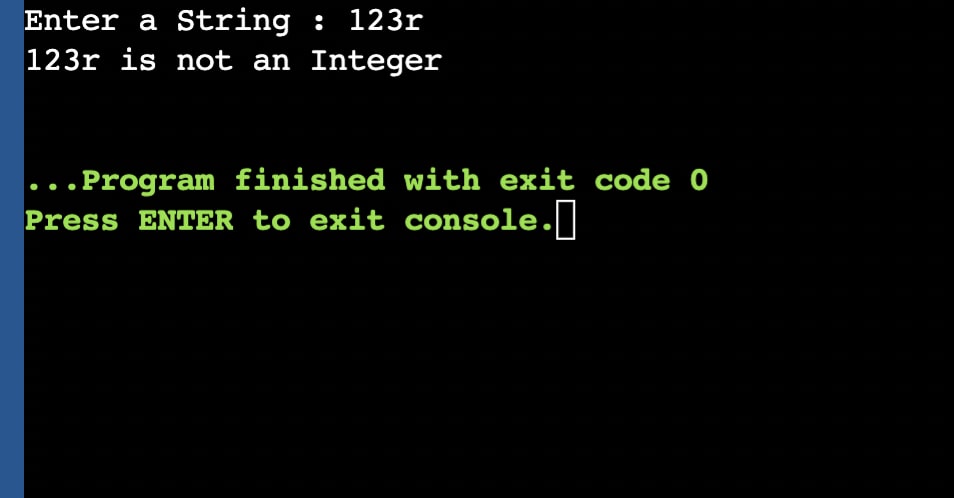
DIGITAL ELECTRONIC
There is a good reason why computer science is a popular field of study all across the world. There is always a demand for computer scientists who can think outside the box and come up with new and better methods to use technology. There are currently computer science programs at nearly every university in Canada. There is, however, the challenge of deciding which colleges have the best programs to choose from. We’ve compiled a list of Canada’s best computer science universities to make your decision a little easier.
Why Study Computer Science in Canada?
Let’s have a look at some compelling arguments in favor of pursuing a degree in computer science after high school in Canada.
- World Class Education: International students seeking to study computer science in Canada benefit from the country’s strong educational system and top-notch faculty. According to QS World Rankings, the best computer science bachelor’s degree programs
- Research Opportunities: Canada’s internationally recognized research center offers many opportunities to work in various research laboratories, including robotics, bioinformatics, and novel interface design, which utilizes numerous mathematics and nature from nature to solve computing problems, among other areas of research.
- Career Opportunities: The number of employment openings in the IT industry is rising, making it a popular career choice for college students. According to the 2018 Canadian ICT industry profile, the country’s IT sector employs more than 6,52,000 workers in the Information Technology sector.
Course Structure
If you’re one of the many students who aim to study computer science in Canada after graduating from high school, you’ll need to familiarize yourself with the course structure of Bachelor’s Computer Science programs in Canada.
- Course Duration: In Canada, a bachelor’s degree in computer science might take anywhere from three to four years to complete. Canadian institutions also offer Computer Science Bachelor programs with majors, specialties, and co-op, which offers a wide range of supplementary courses and internship options for students.
- Content: Canada’s Bachelor of Science in Computer Science (BSc in Computer Engineering) is an engineering degree that focuses on computer science. Content includes algorithm analysis, computer graphics, and human-computer interface; database ideas; encryption and cryptographic systems as well as software engineering, among other things.
- Alternatives: Additionally, you may be able to pursue a Bachelor of Computer Science (BCS) degree in an alternative field, such as a Bachelor of Science (BSc) or Bachelor of Engineering (BEng).
Top 10 Computer Science Universities in Canada

University of British Columbia
Finally, the University of British Columbia completes the list. They have a breathtaking location and a top-notch computer science program. This university is known for both of these things. The university’s Department of Computer Science was founded in 1968 and is one of Canada’s most prestigious research centers. It is possible to pursue a Combined Major in Business and Computer Science for undergraduates. The University of British Columbia is a great place to study computer science because of its vast and diversified student body, excellent location, and high reputation.
University of Toronto
The University of Toronto is the next stop on our tour. Over the past half-century. In the QS World University Rankings, the university is consistently ranked among the world’s top 25 computer science institutions, but this year it managed to get into the top 10. According to a recent report, the percentage of international students at the University of Toronto is predicted to reach 20% by 2021/
University of Waterloo
In Canada, the top computer science program is a three-way tie! This is the first university to be mentioned. With more than 70 courses to select from, and more than 80 industry experts on staff. As a student at college, students can earn up to two years of paid job experience through co-op. There are hundreds of local enterprises looking for computer scientists.
McGill University
At McGill University came in at number four on the list of the best institutions and colleges in Canada. More than 100 master’s degree students and 60 Ph.D. students make up McGill’s School of Computer Science.There are 10 computer science programs at McGill, including the opportunity of working on a paid work term to get significant real-world experience. It’s hard to argue with the university’s location, which is ranked among the top six student cities in the world by QS.
University of Alberta
The University of Alberta’s Department of Computing Science is one of the largest in the country. A decade before the first personal computer was released, it was formed. Robotics, artificial intelligence, and computer graphics are all examples of these are just a few of the topics covered by the department today. Even a few of the world’s most famous people’s fastest computers have been developed at the University of Alberta. As a side note, a team of computer scientists from the University of Alberta has developed technology for supercomputers used by the US government.
University of Montreal
What if science could tell you that, by the year 2050, your house will be at considerable risk of flooding due to climate change? This is what Scientists at the University of Montreal are making an effort to do just. Students at abilities Mobile and wireless communication, animated film and television, and robotics are just a handful of the fields in which graduates find work after graduation.
Simon Fraser University
If you’re looking to get into computer science and don’t think Simon Fraser University in Burnaby, British Columbia is your top choice, you’d be wrong. The award-winning research facilities at Simon Fraser University are known around the world. An estimated 19% of the university’s students are from outside the United States. Zhejiang University in China is a unique partner in the computer science curriculum.
University of Victoria
It’s not just the mildest climate in Canada. The University of Victoria understands how many opportunities students have with a computer science degree. Students can participate after graduating, students must participate in the department’s co-op program in order to gain the requisite work experience. With the use of cutting-edge technologies like machine learning and software, students can form meaningful connections with business leaders development.
University of Calgary
Students By addressing issues, researchers at the University of Calgary are hoping to mold the future of augmented reality. Volunteering at the university’s leading research labs or taking a research course are two other ways that students interested in computer science research can gain practical experience. The University of Calgary has a large number of computer science students (UC). In addition to medical and veterinary occupations, law and education are popular choices for graduates.
McMaster University
It is no surprise that the Faculty of Engineering at McMaster University oversees the computer science degree. As a result, students will learn about information systems architecture and database creation, in addition to programming. This university in Hamilton, Ontario, is renowned for its mechatronics and software engineering programs, as well as eHealth specialties. Best of all, graduates of McMaster may look forward to a promising career. Within two years of graduating, all computer science graduates are employed, a remarkable statistic.
Eligibility
In Canada, a two-year master’s degree in computer science is standard. Jobs such as, and many more are all possible with an M.Eng. or MS in Computer Science from a Canadian university. Below, we’ve listed all of Canada’s requirements for computer science graduate admissions:
- 4 years of undergraduate studies in the appropriate discipline.
- A cumulative grade point average of at least 75% during the final four semesters or the whole bachelor’s degree program.
- To be considered for a master’s degree program, an applicant must have passed the university’s specific entrance exam.
- Work experience in the selected master’s field for at least one year.
- scores on standardized tests of English linguistic ability.
- A copy of one’s official academic record.
- If available, a diploma or certificate from previously completed part-time courses.
Cost of Studying
According to several sources, the annual tuition for a Bachelor in Computer Science in Canada ranges from CAD 1,535 to 55,500 Hence, we hope that this blog has helped you discover the best colleges in Canada for Computer Science courses, with the top institutions in Canada for Computer Science on the list provided. Leverage Edu professionals can help you discover a degree program and university in Canada that suits your needs, as well as guide you through the application process to guarantee that you get shortlisted!
Cost of Living
Between 850 CAD to 1,575 CAD per month, students must also pay for their living expenses. The majority of students’ expenses come from housing, which can cost anywhere from $4,000 to $8,750 per year depending on whether you live on or off campus.
The post Top 10 Computer Science Universities in Canada 2022 appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/EzXeQgk