In today’s era Network or Internet is used to send and receive data worldwide. As we know the network is a complex structure consisting of lots of computers and networking devices.
The system which seeks data is known as the Client and the system which provides the data is known as Host.
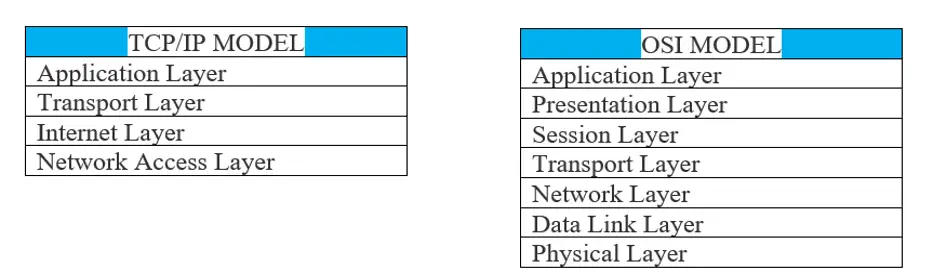
Also, we know that the TCP/IP and OSI models are the models which are used most. Both use layer architecture.
Before transmission data moves between these layered architectures. Encapsulation and decapsulation are two processes used in this layered architecture. It’s like Boxing and Unboxing a real-world object for sent over courier.
We can’t send any data directly on the internet. There are lots of things to do before transmission, like establish host to host communication, provides source and destination IP addresses etc. Fortunately, we as a user do not need to do any chores. The Network model does the credits. All we need to do is to just select the data and press “send or upload”.
Encapsulation
It is a process in which additional information is added with the original data packet which is required for accurate and safe transmission of data over the Internet.
Here encapsulation could be described as a method of designing modular communication protocols. These protocols are used to create Protocol Data Unit (PDU). These PDU are being attached with the original data packet, which is forwarded over the internet. These PDU are created by the layers of the network model such as TCP/IP and OSI. Each layer has its own unique PDU and performs the task as per the layer’s functioning.
When we select data for transmission, the layers start their work step by step. The selected data move downwards in these layers. At every layer some new kind of data (Not the user data, the system data like IP addresses, frame size etc.) also known as PDU, is added with the original data packet (Selected by user). So, this whole process in known as Encapsulation.
Let’s take an example.
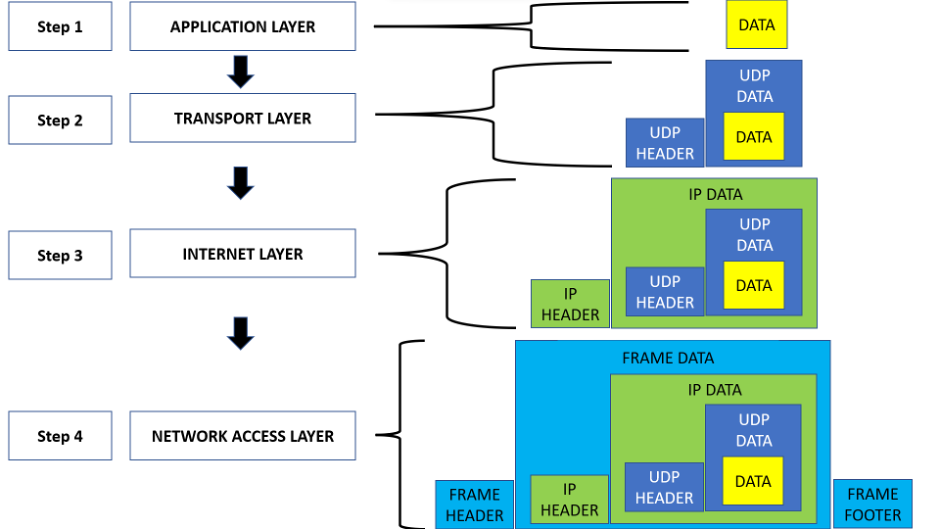
Here in this example, the user uses TCP/IP model.
Here in above mentioned diagram, the yellow-coloured box is user data, which he/she wants to send over the network. When the user press sends or upload from his device, the data is forwarded to the Application layer.
This is step 1. Here Data itself is a PDU in this stage. The application layer shows the data to the user, received from the network in a format, which is easy to understand for the user. Every facility like email service, internet surfing l, online shopping, etc is falling into this category.
In step 2, the data packet is forwarded to the transport layer, where the data is encapsuled by the UDP (User Datagram Protocol) data. As you can see in the above diagram. Also, the UDP header is attached for identification of UDP data packet. Here this PDU is known as a segment.
In 3rd step, the segment is sent to the Internet layer. Here the segment is encapsulated by the IP data and the IP header is attached. This is the PDU of this layer.
This PDU is known as Packet. Each and every device or system in the network has an individual and unique IP address. IP header is responsible for containing source and destination IP addresses. These details are used to search and find out the location of the client and host in the network.
In 4th step this packet is sent to the Network Access Layer. Here the received data packet is encapsulated by the MAC address. Now this PDU is called Frame. Each frame has Frame Header and Footer. MAC Address or Media Access Control actually represents a real-world hardware or physical address of the Network Adapter or system like the computer of a host. This address or hardware ID is allotted by the Manufacturer of the NIC (Network Interface Card).
Once the 4th step is completed the frame is sent over the network. So, as we can see in the above diagram the original data is encapsulated by much additional information in each stage. This data or information addition is known as Encapsulation.
Each layer encapsule the original data with its own PDU, and this whole PDU is again encapsulated in a new PDU at the next stage. The process continued till the last layer arrived.
Decapsulation
This is the reverse process of encapsulation. In this, the additional information is plucked out from the original data. Once the frame reached at its destination or the host system, the reverse process is started. This is down to top approach, where the frame is received by the network layer first and then after decapsulation, it is sent to the upper layer such as Internet layer.
Similar to Encapsulation each layer has its own Decapsulation format. For example, take the above-mentioned figure but this time it will be in reverse order such as given below:
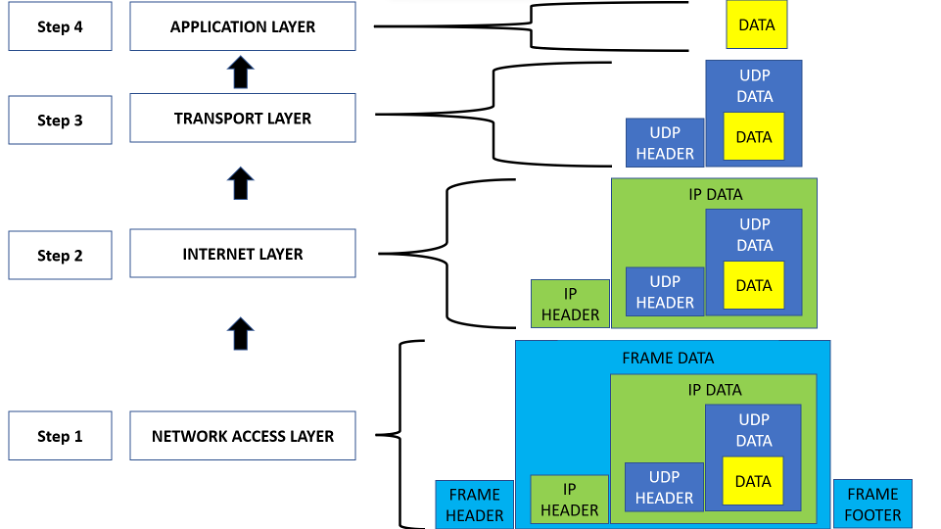
At 1st step the frame is sent from the client, and received by the network layer of the host computer. This PDU or frame is removed, and only this PDU Packet is forwarded to the Internet layer.
In step 2 the packet is decapsulated and the Packet PDU is removed and now it is the segment PDU. This is forwarded to the Transport layer.
In step 3 the segment is again decapsulated and the PDU segment is removed and finally, the original data is forwarded to the Application layer.
In step 4 the original data is shown to the user.
Both processes are related and necessary for smooth and secure data transmission over the network.
Difference between Encapsulation and Decapsulation
| Encapsulation | Decapsulation |
| It follows Top to Down approach; the data moves in sequence between layers but goes down layer from the recent upper one. | It follows Down to TOP approach; the data moves in sequence between layers but goes upward layer from the recent down one. |
| In each layer the additional information is added with the original data. | In each layer the additional information is removed till the original data is decapsulated. |
| At each step the size is increased. | At each stage the size is decreased. |
The encapsulation technique and Decapsulation technique are used to secure the original data and provide 100% secure and successful data transmission.
The post Encapsulation and Decapsulation in Networking appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/wGdo8VS
Post a Comment